Meta Confirms Zero-Click WhatsApp Spyware Attack Targeting 90 Journalists, Activists
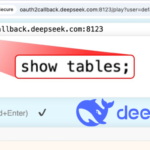
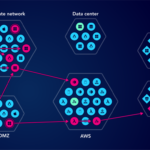
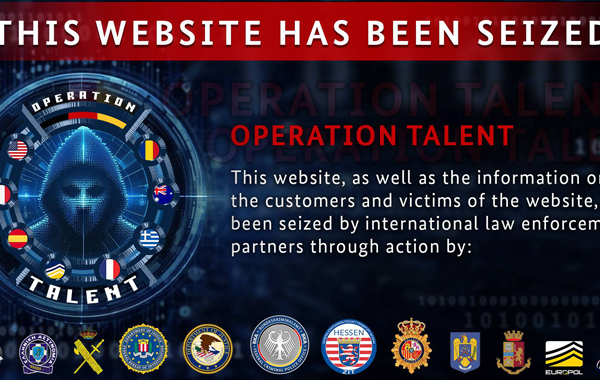
Meta-owned WhatsApp on Friday said it disrupted a campaign that involved the use of spyware to target journalists and civil society members. The campaign, which targeted around 90 members, involved the use of spyware from an Israeli company known as Paragon Solutions. The attackers were neutralized in December 2024. In a statement to The Guardian,…