CISA Adds NAKIVO Vulnerability to KEV Catalog Amid Active Exploitation
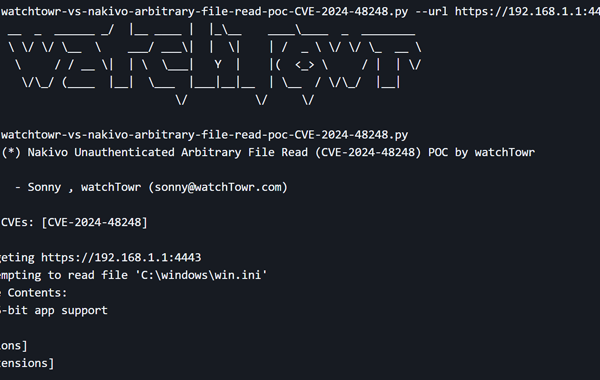
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity security flaw impacting NAKIVO Backup & Replication software to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability in question is CVE-2024-48248 (CVSS score: 8.6), an absolute path traversal bug that could allow an unauthenticated attacker to