RansomHub Becomes 2024’s Top Ransomware Group, Hitting 600+ Organizations Globally
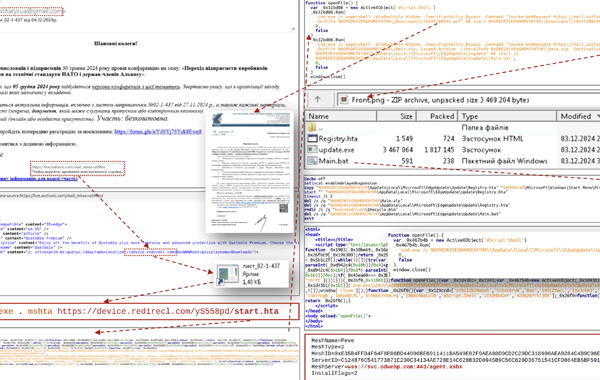
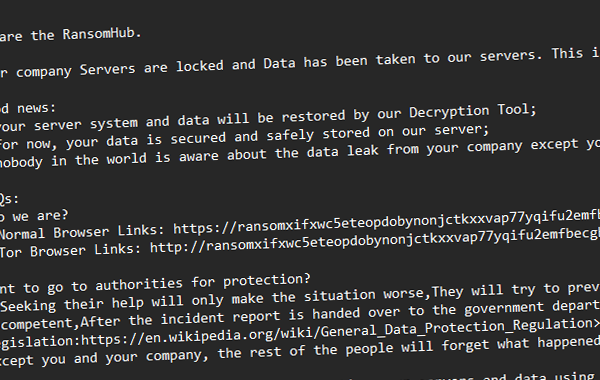
The threat actors behind the RansomHub ransomware-as-a-service (RaaS) scheme have been observed leveraging now-patched security flaws in Microsoft Active Directory and the Netlogon protocol to escalate privileges and gain unauthorized access to a victim network’s domain controller as part of their post-compromise strategy. “RansomHub has targeted over 600 organizations globally, spanning sectors